


SECURITY
AUTOMATED
Automotive and IoT cybersecurity software to effortlessly harden and monitor your devices.
CRATETM Remote Cybersecurity Testing Platform


Fastest and Lowest Cost Approach to Cybersecurity Testing
- Validation, Vulnerability, & Penetration Testing
- Fuzzing automation tools
- Bug bounties! First platform to enable remote bug bounties for IoT
- Limited availability of testers solved by remote access
- Extremely effective for large devices
- Designed for ISO/SAE 21434, FDA SPDF, IEC 81001-5-1
- Testing services & consulting available using CRATE
Services for Regulatory Compliance & Testing
Regulations are in effect requiring cybersecurity for both Automotive and Medical Devices. BG Networks cybersecurity experts help minimize the time needed with tasks ranging from installing a Secure Product Development Framework to penetration testing.
Access
Threat and risk assessment, security training, and regulatory advisement services
Design
BGN-SAT Security Automation Tool makes security by design easy: secure boot, encryption, hardware based security
Test
Penetration testing and security validation for regulatory compliance, certification, and brand protection
Manufacture
Streamlined handoff from design to production: foolproof provisioning and key management
Monitor
AnCyR sets the new host-based, real-time intrusion detection standard for accuracy, false positives, and low overhead


Automotive
Software tools and services supporting ISO/SAE 21434 & UN R155 certification. ECU Hardening, Penetration Testing, Real-Time Monitoring, and Compliance Consulting


Medical Devices
Medical device cybersecurity and services for newly mandated FDA submission requirements
AWARD-WINNING TOOLS
BG Networks' award-winning embedded systems security solutions and services help engineers harden, monitor, and protect products while meeting regulatory compliance throughout the entire lifecycle.
![]()

BGN-SAT Security Automation Tool
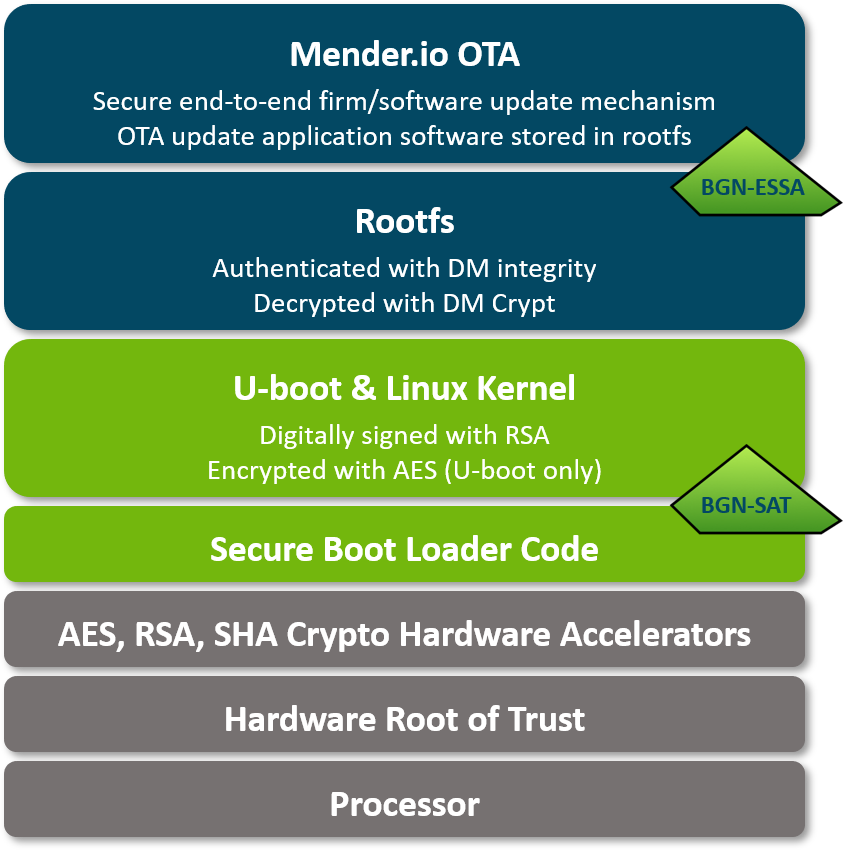

- Fully leverage the security features in today's embedded processors
- Easy to use GUI-based tool
- Secure Boot, Authentication, Encryption, Interface Security
- Seamless transition from design to manufacturing with one click provisioning and key management
AnCyRTM Anomaly Detection and Cyber Resilience Host-based IDPS
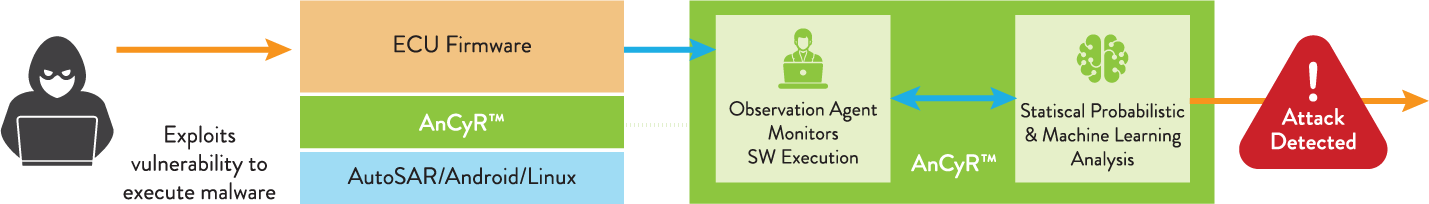

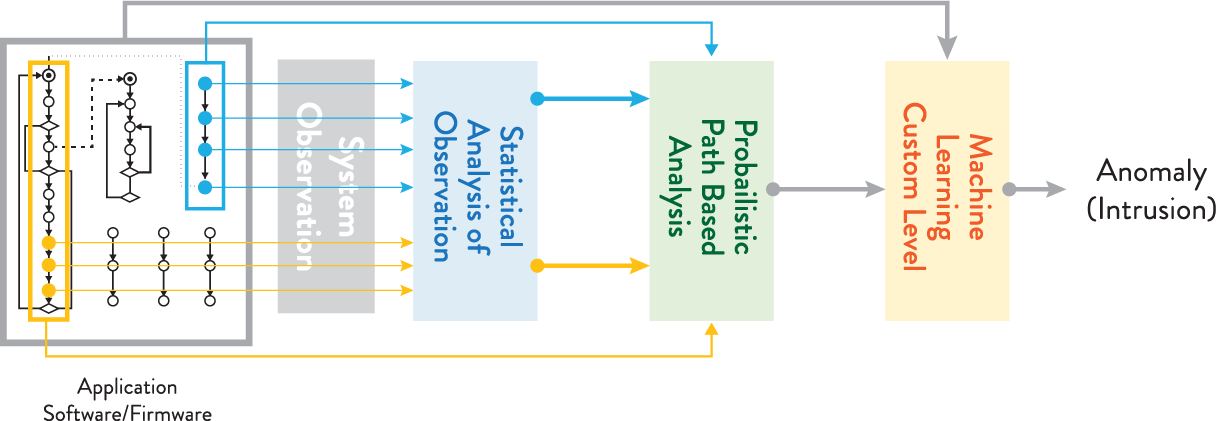

- Host-based anomaly detection optimized for automotive ECU intrusion detection (IDPS)
- Sets new standards for real-time detection, accuracy, and low false positives
- Low latency and overhead optimized for embedded applications
- Automated training using AI & ML to optimize model accuracy
Embedded Security Consulting
- Regulatory Compliance Advisement
- ISO/SAE 21434 and UN R155
- TARA (Threat Agent Risk Assessment)
- Penetration Testing
- Broad embedded cybersecurity support from assessment and development to validation and deployment
Cybersecurity Workshops
- Hands-on workshops that cover the critical topics of embedded systems and device cybersecurity
- Address the biggest challenges of implementing IoT cybersecurity
- No previous cybersecurity experience required
- Lengths and content customized to your needs










